The team of developers responsible for the operation of the AirSwap protocol, through which the decentralized exchange of tokens of the ERC-20 standard is organized, reported the detection of a critical bug in the smart contract that was integrated with the Ethereum core network. The developers reported on their findings, as well as on a possible solution to the problem, in a Medium post.
A critical bug detected in a smart contract would allow an attacker to swap without the need to obtain a signature from the counterparty. It is known that the bug remained in the AirSwap system for about 24 hours, that is, from noon on September 11 until noon the next day. The team found that about 20 user addresses could be affected by this bug, the developers managed to take some measures, however, another 10 accounts remain in the risk zone.
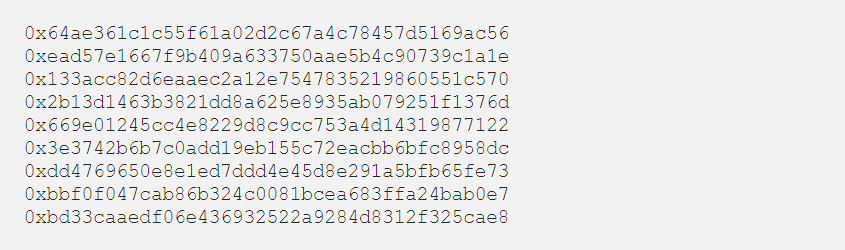
As a result, the developers returned the version that was used before the update, at present, no one is in danger except for the owners of 9 accounts that are indicated in the post from AirSwap. Owners of the above accounts must cancel authorization in the damaged smart contract, following the instructions.